███████╗ █████╗ ███╗ ██╗ ██████╗ ███████╗██╗ ██╗ ██╔════╝██╔══██╗████╗ ██║ ██╔══██╗██╔════╝██║ ██║ ███████╗███████║██╔██╗ ██║ ██║ ██║█████╗ ██║ ██║ ╚════██║██╔══██║██║╚██╗██║ ██║ ██║██╔══╝ ╚██╗ ██╔╝ ███████║██║ ██║██║ ╚████║██╗██████╔╝███████╗ ╚████╔╝ ╚══════╝╚═╝ ╚═╝╚═╝ ╚═══╝╚═╝╚═════╝ ╚══════╝ ╚═══╝

Imagine you wake up on a normal morning, ready to get on with your day. You get out of bed and decide to reach for that one object more greater in importance than life itself: your mobile phone. Still half-asleep, your fingers perform a tap dance on a screen in an attempt to get a much needed dopamine hit either through Facebook or TikTok or Youtube.
Much to your dismay, you panic as you notice a billion email notifications which contains phrases such as “account password changed”, “security information updated”, “unusual activity detected”.
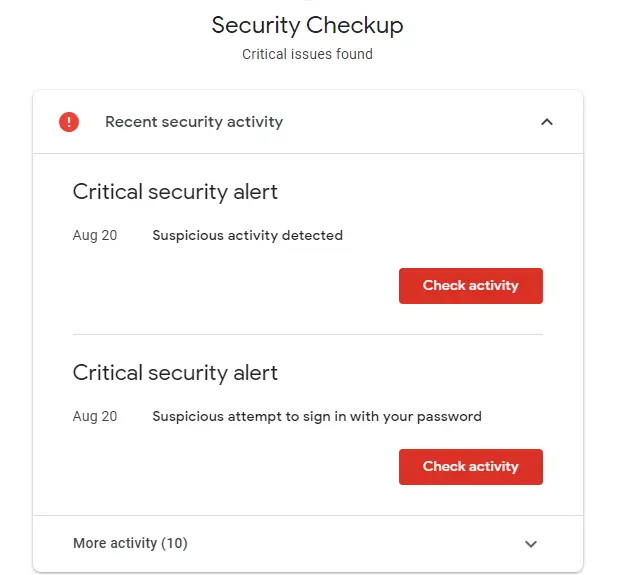
Unfortunately, you have just fallen victim to a credential stuffing attack overnight. A credential stuffing attack is a type of cyberattack where a cybercriminal uses a large collection of stolen account credentials known as combo-lists (which contains thousands of lines of credentials usually in a email:password format), to attempt to gain access to other applications.
Earliest reports of credential stuffing attacks can be traced back to around 2014, when hackers on the dark web started offering services that can anonymously validate individual credential sets against specific companies.
During the 2020 coronavirus pandemic, the rate and popularity of credential stuffing attacks exploded, especially due to the high growth of “cracking” forums such as Nulled[.]to and Cracked[.]io which were recently taken down in a combined effort by a conglomerate of international security agencies with the campaign codenamed “Operation Talent“.
Unlike the earlier days where cybercriminals could only perform checks to see whether an individual or small quantity of login details were valid against other online services, modern day surface web marketplaces such as Nulled provided its thousands of active users the ability to purchase accounts for services such as compromised details for digital streaming services such as Netflix, Hulu and Spotify to even fast food rewards services such as McDonalds and Firehouse Subs.
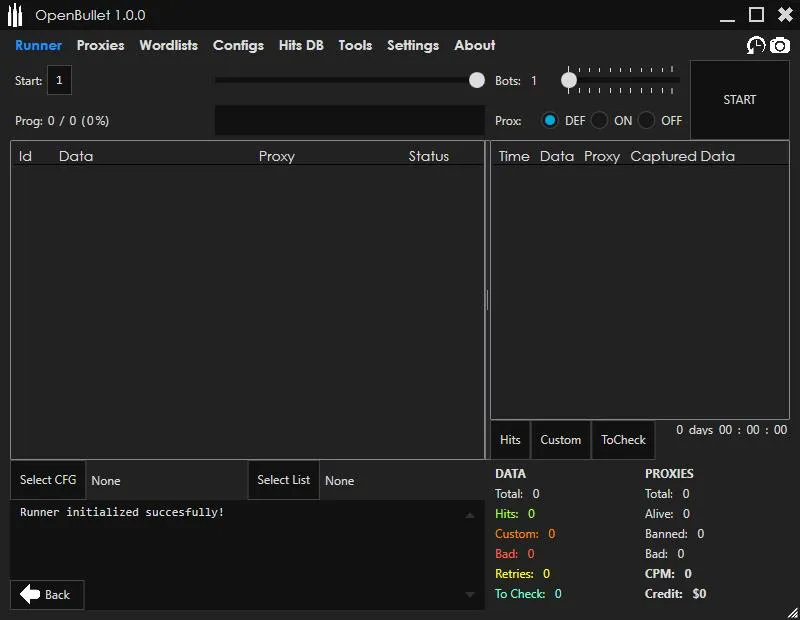
For the more technologically capable, these marketplaces often sold tools and guides on taking existing credential lists gathered from data breaches and automating their validation against other online services such as the ones listed above. A common tool that is utilised in these attacks is known as OpenBullet.
OpenBullet is an open-source web testing application which allows the end user to perform actions such as scraping information, penetration testing and automate/mimic human interaction through Selenium.
Although the clear disclaimer on their Github repository states that performing DDoS and credential stuffing attacks using OpenBullet is illegal, the tool’s “Runner” function allow users to take data such as a combo list and utilise a “config”, which is a file that contains a set of instructions to target specific online applications, to perform automated credential stuffing attacks to determine whether accounts within the original combo-list are valid on their platform.
As many online applications would “time-out” the source IP address/session after multiple failed login attempts, the OpenBullet application also provides the function to distribute the attacks over a set of proxies, which are also another service sold on illegal marketplaces such as Nulled and Cracked. These proxies allows attackers to obfuscate their true source IP address by relaying the attacks over a pool of IP addresses, which further increases their success rate by effectively jumping over the hurdles put in place by application security features such as API timeouts and reputation-based IP address blacklisting.
So you might be asking yourself, what can YOU do to protect yourself against these types of attacks? The easiest way to protect against credential stuffing attacks is to make use of a secure password manager to ensure that each website/application has a unique password and no two platforms use the same password. This is an extremely easy way to ensure that in the case of a security breach of a website, the leaked credentials are only specific to that website and cannot be used elsewhere. It is also extremely important that two factor authentication is used on supported online services, so that even in the case of breach of credentials, attackers would not be able to gain access to your account as the 2FA/MFA would act as a second layer of defence. You can also use services such as HaveIBeenPwned to check whether your credentials have been located in various data breaches found distributed online.
For the developers of online applications, there are effective countermeasures that can be employed to negate/prevent the use of credential stuffing attacks against your platform.